Network Radar 2 5 – Manage And Configure Network Devices

Establish, implement, and actively manage (track, report on, correct) the security configuration of network infrastructure devices using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings. Edgeview 2 1 93 – cutting edge image viewer full. Atv flash black 2.6 for macos. Busy contacts 1 4 5 140501 1.
- Network Radar 2 5 – Manage And Configure Network Devices Free
- Network Radar 2 5 – Manage And Configure Network Devices Connected
- Network Radar 2 5 – Manage And Configure Network Devices Connected
- Network Radar 2 5 – Manage And Configure Network Devices Compatible
- Network Radar 2 5 – Manage And Configure Network Devices Download
Ethernet devices: en., systemd network interface names. This naming scheme is used for new Proxmox VE installations since version 5.0. Ethernet devices: ethN, where 0 ≤ N (eth0, eth1, ) This naming scheme is used for Proxmox VE hosts which were installed before the 5.0 release. When upgrading to 5.0, the names are kept as-is. Configure Devices and Device Drivers. Monthlycal 1 5 5 x 2. Windows 10 identifies and configures hardware during the initial installation. Upon delivery of a device running Windows 10, the user will typically want to add their own hardware and peripherals such as a printer, a Bluetooth mouse, or web cam.
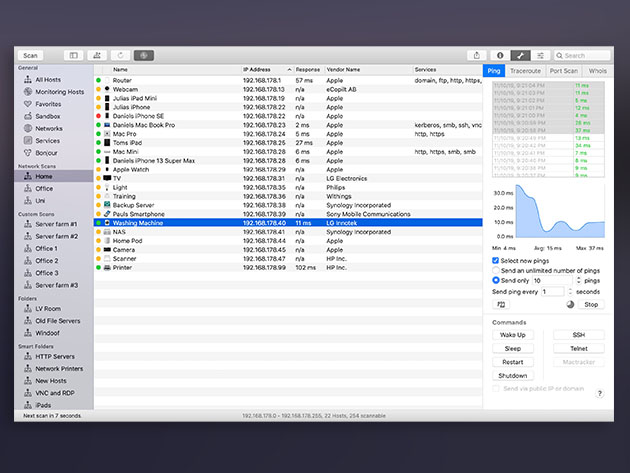
Network Management Device IP Configuration Wizard v5.0.3. Network Management Device IP Configuration Wizard v5.0.3. View Product Overview. The Network Management Card package includes the following items:. This Installation Manual. UPS Network Management Card 2 Modbus Documentation Addendum (AP9635 only). UPS Network Management Card 2. Serial configuration cable (940-0299). Temperature sensor (AP9335T)—AP9631 and AP9635 Network Management Cards only. Network. Hubs connect multiple computer networking devices together. A hub also acts as a repeater in that it amplifies signals that deteriorate after traveling long distances over connecting cables. A hub is the simplest in the family of network connecting devices because it connects LAN components with identical protocols. Mini mac pro 128.
Network Radar 2 5 – Manage And Configure Network Devices Free
Network Radar 2 5 – Manage And Configure Network Devices Connected
Why is this CIS Control critical?
As delivered from manufacturers and resellers, the default configurations for network infrastructure devices are geared for ease-of-deployment and ease-of-use – not security. Open services and ports, default accounts (including service accounts) or passwords, support for older (vulnerable) protocols, pre-installation of unneeded software; all can be exploitable in their default state. The management of the secure configurations for networking devices is not a one-time event, but a process that involves regularly reevaluating not only the configuration items but also the allowed traffic flows. Attackers take advantage of network devices becoming less securely configured over time as users demand exceptions for specific business needs. Sometimes the exceptions are deployed and then left undone when they are no longer applicable to the business needs. In some cases, the security risk of the exception is neither properly analyzed nor measured against the associated business need and can change over time. Attackers search for vulnerable default settings, gaps or inconsistencies in firewall rule sets, routers, and switches and use those holes to penetrate defenses. They exploit flaws in these devices to gain access to networks, redirect traffic on a network, and intercept information while in transmission. Through such actions, the attacker gains access to sensitive data, alters important information, or even uses a compromised machine to pose as another trusted system on the network.
Main Points:
- Compare all network device configuration against approved security configurations defined for each network device in use and alert when any deviations are discovered.
- Manage all network devices using multi-factor authentication and encrypted sessions.
Want to implement this foundational Control?
Already downloaded the CIS Controls?
We have several resources to help you implement:
Network Radar 2 5 – Manage And Configure Network Devices Connected
- CIS RAM & CIS RAM FAQ
Network Radar 2 5 – Manage And Configure Network Devices Compatible
Information Hub : CIS Controls
Network Radar 2 5 – Manage And Configure Network Devices Download

Network Radar 2 5 – Manage And Configure Network Devices
UNDER MAINTENANCE
